Azure-Advanced-Networking
M07-Unit 5 Restrict network access to PaaS resources with virtual network service endpoints
Virtual network service endpoints enable you to limit network access to some Azure service resources to a virtual network subnet. You can also remove internet access to the resources. Service endpoints provide direct connection from your virtual network to supported Azure services, allowing you to use your virtual network’s private address space to access the Azure services. Traffic destined to Azure resources through service endpoints always stays on the Microsoft Azure backbone network.
In this exercise, you will:
- Task 1: Create a virtual network
- Task 2: Enable a service endpoint
- Task 3: Restrict network access for a subnet
- Task 4: Add additional outbound rules
- Task 5: Allow access for RDP connections
- Task 6: Restrict network access to a resource
- Task 7: Create a file share in the storage account
- Task 8: Restrict network access to a subnet
- Task 9: Create virtual machines
- Task 10: Confirm access to storage account
- Task 11: Clean up resources
Estimated time: 35 minutes
Task 1: Create a virtual network
-
Login to the Azure Portal.
-
On the Azure Portal home page, search for virtual network and then select Virtual network from the results.
-
Select + Create.
-
On the Create virtual networks pane, on the Basics tab, use the information in the following table to create the VNet:
Setting Value Resource Group Create new: Name: myResourceGroup Virtual Network Name CoreServicesVnet Location East US -
Click Next.
-
On the Security blade.Click Next.
-
On the IP addresses blade: In the existing Address space section, check that the address space is set to 10.0.0.0/16
Note: If the Address space is different, then delete and re-create a 10.0.0.0/16 address space.
-
In the Address space section, under Subnets, select Default.
-
On the Edit subnet blade, use the information in the following table to edit the current Subnet (leave others with their default values):
Setting Value Subnet template Default Name Public Starting address 10.0.0.0 Subnet size /24 (256 addresses) -
Click Save
-
Click Review and Create. Let validation occur, and click Create again to submit your deployment.
Task 2: Enable a service endpoint
Service endpoints are enabled per service, per subnet. Create a subnet and enable a service endpoint for the subnet.
-
In the Search resources, services, and docs box at the top of the portal, enter CoreServicesVNet. When CoreServicesVNet appears in the search results, select it.
-
Add a subnet to the virtual network. Under Settings, select Subnets, and then select + Subnet, as shown in the following picture:
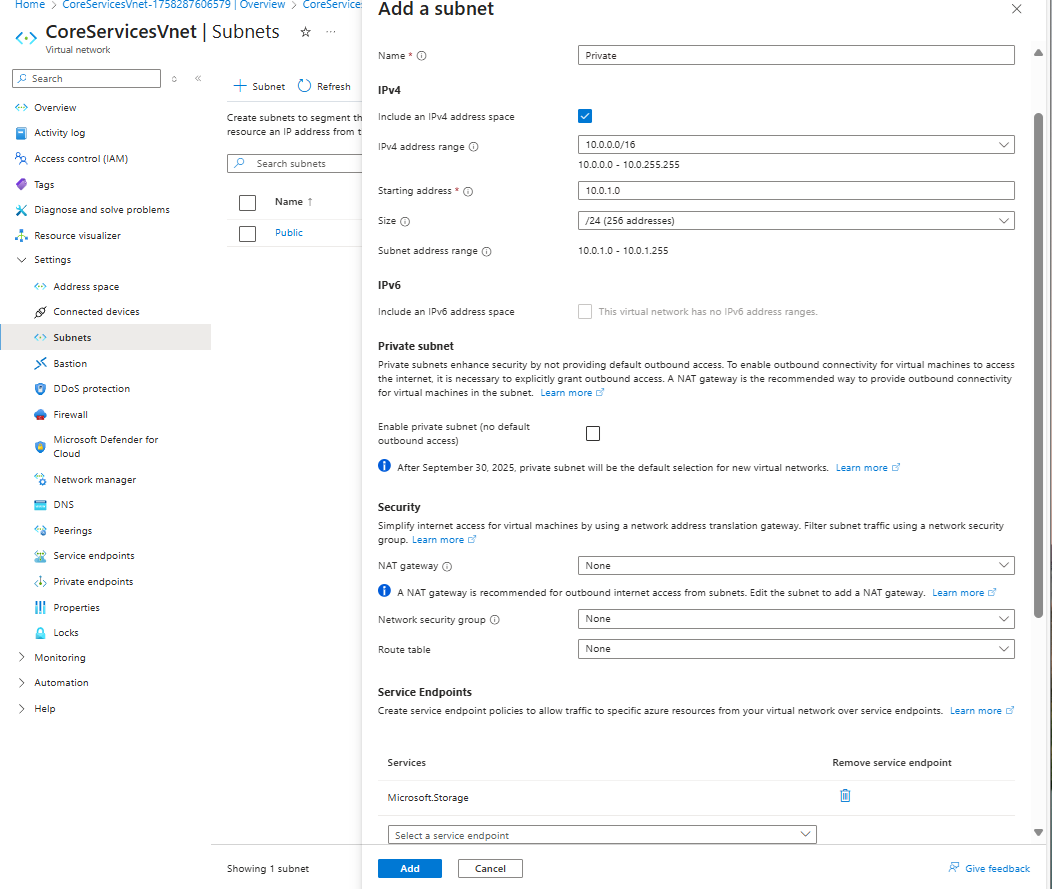
-
Under Add subnet, select or enter the following information:
Setting Value Name Private Starting address 10.0.1.0/24 Service endpoints: Services Select Microsoft.Storage -
Select Add.
You should now have two subnets configured:
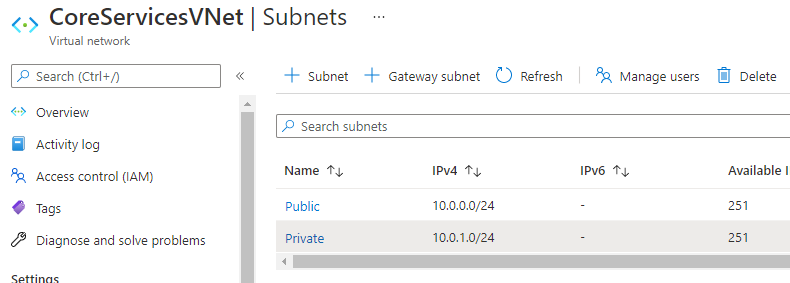
Task 3: Restrict network access for a subnet
By default, all VMs in a subnet can communicate with all resources. You can limit communication to and from all resources in a subnet by creating a network security group and associating it to the subnet.
-
In the Search resources, services, and docs box at the top of the portal, enter security group. When Network Security groups appears in the search results, select it.
-
In Network security groups, select + Create.
-
Enter or select, the following information:
Setting Value Subscription Select: your Subscription Resource group Select: myResourceGroup Name ContosoPrivate-nsg Region East US -
select Review + create, then select Create:
-
After the ContosoPrivate-nsg network security group is created, select Go to resource.
-
Under Settings, select Outbound security rules.
-
Select + Add.
-
Create a rule that allows outbound communication to the Azure Storage service. Enter, or select, the following information:
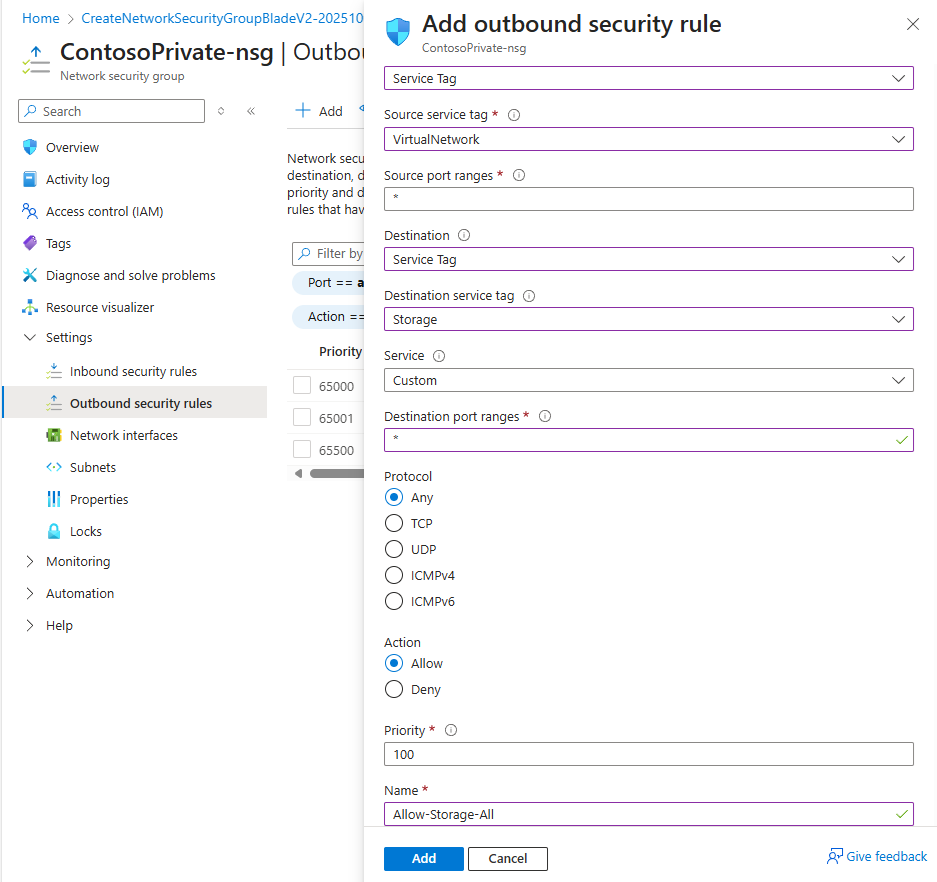
Setting Value Source Select Service Tag Source service tag Select VirtualNetwork Source port ranges * Destination Select Service Tag Destination service tag Select Storage Service Custom Destination port ranges * Protocol Any Action Allow Priority 100 Name Allow-Storage-All -
Select Add:
Task 4: Add additional outbound rules
Create another outbound security rule that denies communication to the internet. This rule overrides a default rule in all network security groups that allows outbound internet communication.
-
Select +Add under Outbound security rules.
-
Enter, or select, the following information:
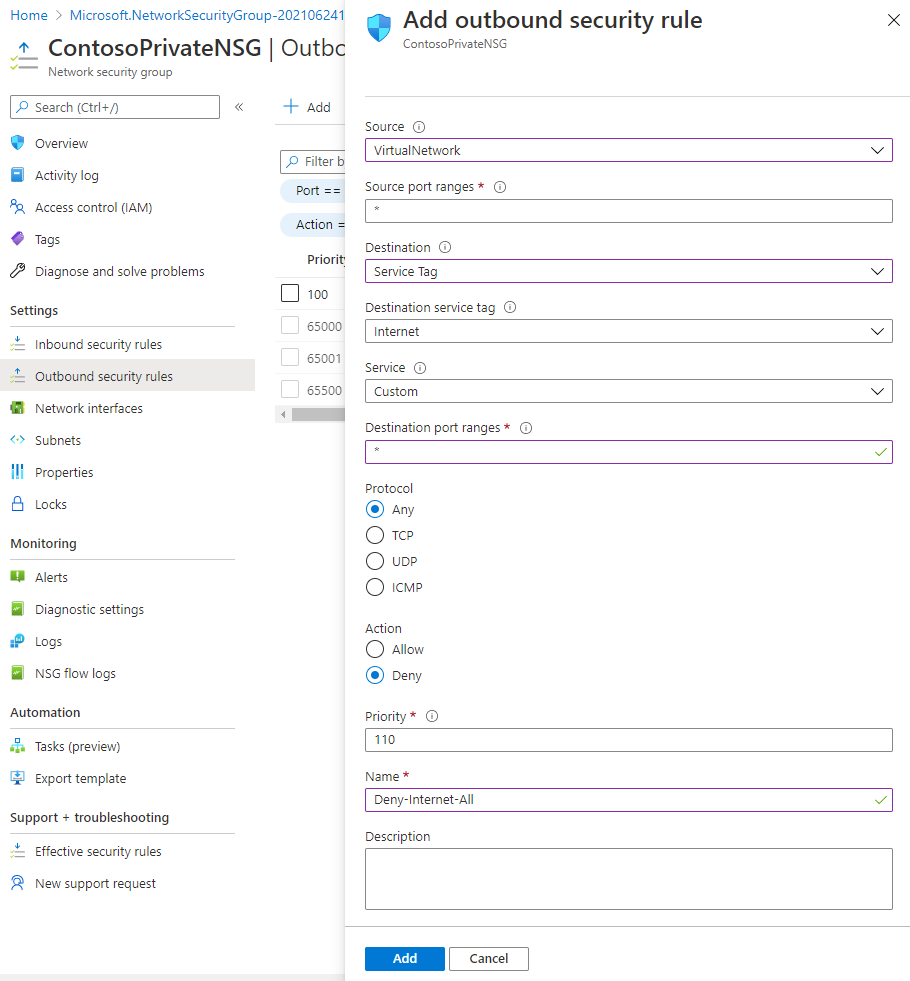
Setting Value Source Select Service Tag Source service tag Select VirtualNetwork Source port ranges * Destination Select Service Tag Destination service tag Select Internet Service Custom Destination port ranges * Protocol Any Action Deny Priority 110 Name Deny-Internet-All -
Select Add.
Task 5: Allow access for RDP connections
Create an inbound security rule that allows Remote Desktop Protocol (RDP) traffic to the subnet from anywhere. The rule overrides a default security rule that denies all inbound traffic from the internet. Remote desktop connections are allowed to the subnet so that connectivity can be tested in a later step.
-
On ContosoPrivateNSG | Outbound security rules, under Settings, select Inbound security rules.
-
Select + Add.
-
In Add inbound security rule, enter the following values::
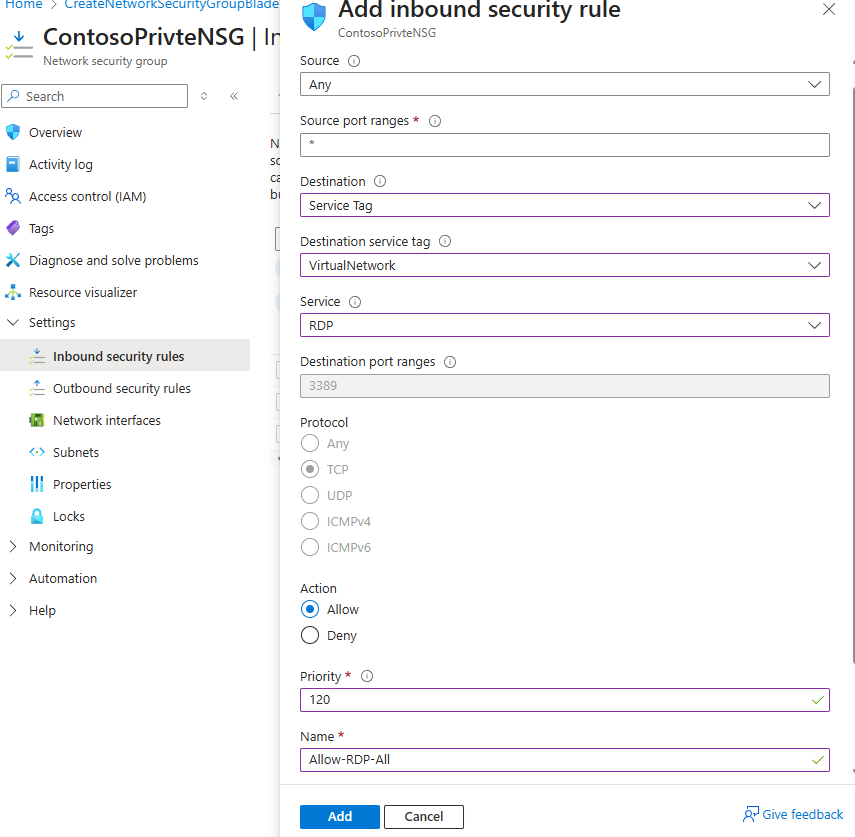
Setting Value Source Any Source port ranges * Destination Select Service Tag Destination service tag Select VirtualNetwork Service Select RDP from drop down List Action Allow Priority 120 Name Allow-RDP-All -
And then select Add.
Warning: RDP port 3389 is exposed to the Internet. This is only recommended for testing. For production environments, we recommend using a VPN or private connection.
-
Under Settings, select Subnets.
-
Select + Associate.
-
Under Associate subnet, select Virtual network and then select CoreServicesVNet under Choose a virtual network.
-
Under Choose subnet, select Private, and then select OK.
Task 6: Restrict network access to a resource
The steps necessary to restrict network access to resources created through Azure services enabled for service endpoints varies across services. See the documentation for individual services for specific steps for each service. The remainder of this exercise includes steps to restrict network access for an Azure Storage account, as an example.
-
On the Azure portal, select Storage accounts.
-
Select +Create.
-
Enter, or select, the following information and accept the remaining defaults:
Setting Value Subscription Select your subscription Resource group myResourceGroup Name contosostoragexx (where xx are your initials to make it unique) Region East US Performance Standard (general purpose v2)** Redundancy Locally-redundant storage (LRS) -
select Review, then select Create.
Task 7: Create a file share in the storage account
-
After the storage account is created, Select Go to resource.
-
In the Storage account blade, under Data storage.
-
Select File shares, and select + File share.
-
On the New file share blade Enter marketing under Name, and then select Next : Backup., as shown in the following picture:
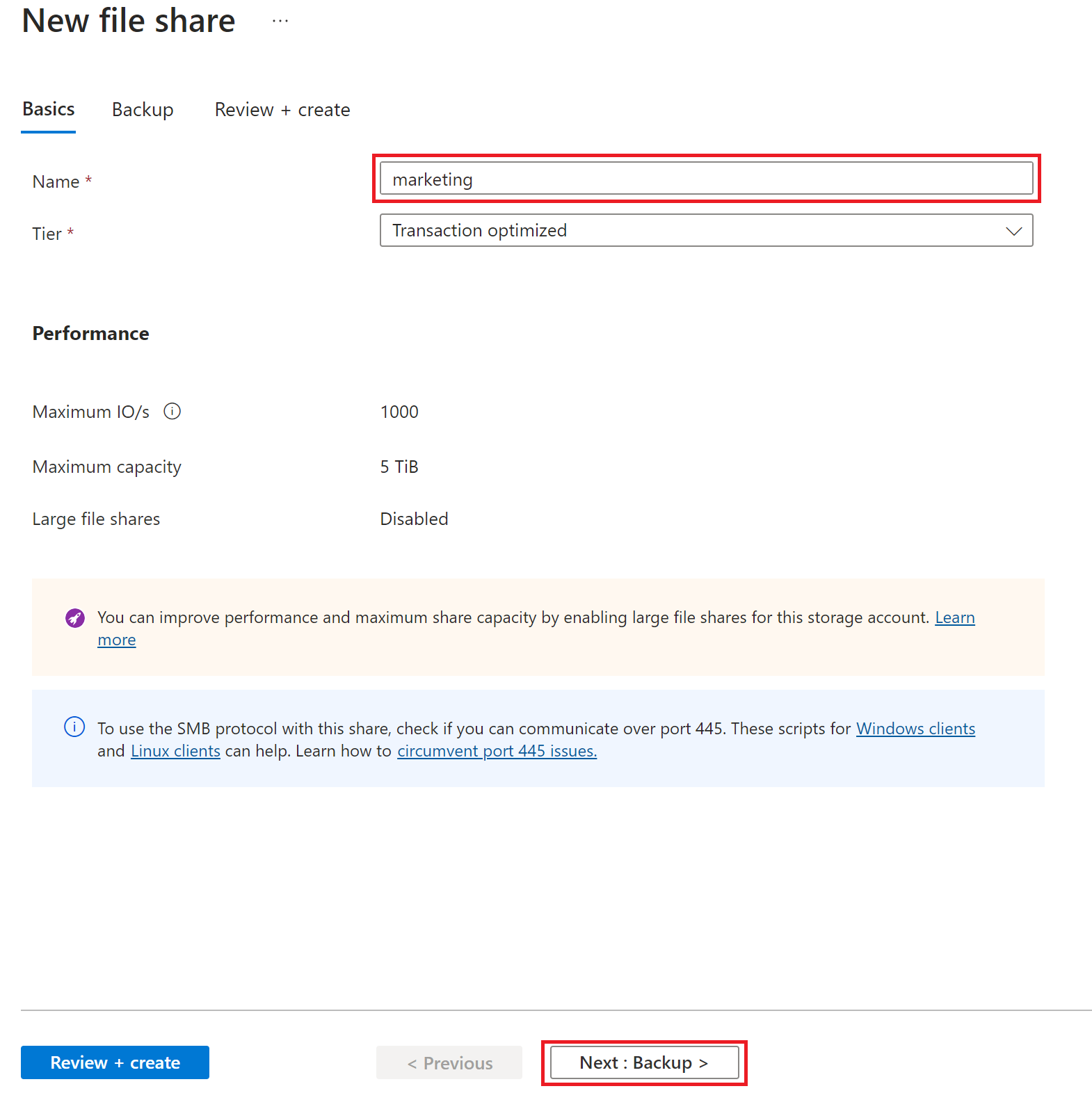
-
On the Backup tab, De-Select the Enable backup tickbox
-
Select Review + Create, and when validation has passed, select Create
-
Go back to the overview page of the contosostoragexx storage account.
Task 8: Restrict network access to a subnet
By default, storage accounts accept network connections from clients in any network, including the internet. Deny network access from the internet, and all other subnets in all virtual networks, except for the Private subnet in the CoreServicesVNet virtual network.
-
In the contosostoragexx Storage Account.
-
Under Security + networking for the storage account, select Networking.
-
Select Manage
-
Next to
Public network access scopeselect the Enable from selected networks radio button**. -
Under Virtual networks , click + Add a virtual network and Add existing virtual network.
-
on the Add network blade select:
Setting Value Subscription Select your subscription. Virtual networks Select CoreServicesVNet. Subnets Select Private.
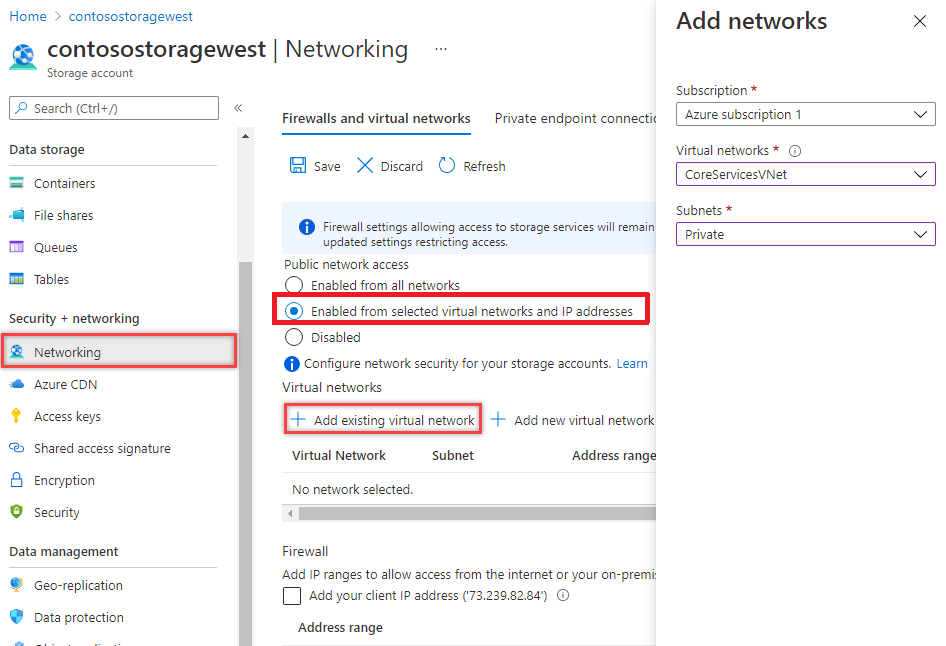
-
Select Enable then Add.
-
Select Save.
-
Under Security and Networking for the storage account, select Access keys.
-
Select Show for key1. Copy the key to Notepad as you’ll have to manually enter it in a later step when mapping the file share to a drive letter in a VM.
Or, you can copy from here later when required.
Task 9: Create virtual machines
To test network access to a storage account, deploy a VM to each subnet.
-
On the Azure portal, open the PowerShell session within the Cloud Shell pane.
-
In the toolbar of the Cloud Shell pane, select the Upload/Download files icon, in the drop-down menu, select Upload and upload the following files VMs.json and VMs.parameters.json into the Cloud Shell home directory one by one from the source folder F:\Allfiles\Exercises\M07.
-
Deploy the following ARM templates to create the VMs needed for this exercise:
$RGName = "myResourceGroup" New-AzResourceGroupDeployment -ResourceGroupName $RGName -TemplateFile VMs.json -TemplateParameterFile VMs.parameters.json -
When prompted for the adminpassword enter Pa55w.rd1234abc.
-
When the deployment is complete (the deployment can take a few minutes), Minimise Cloud Shell and then go to the Azure portal home page, and then select Virtual Machines.
Task 10: Confirm access to storage account
-
Once the ContosoPrivate VM finishes creating, open the blade for the VM by selecting Go to resource. Select the Connect button, then select RDP.
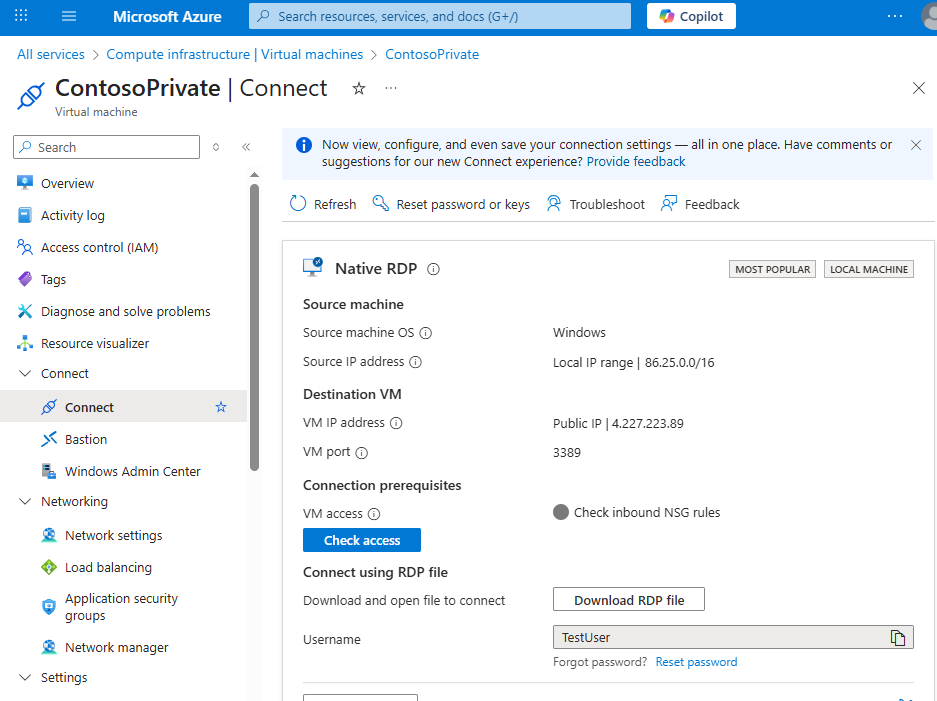
-
After selecting the Connect button and RDP, select the Download RDP File button. A Remote Desktop Protocol (.rdp) file is created and downloaded to your computer.
-
Open the downloaded rdp file. If prompted, select Connect. Enter the user name: Testuser and password: Pa55w.rd1234abc. You may need to select More choices, then Use a different account, to specify the credentials you entered when you created the VM.
-
Select OK.
-
You may receive a certificate warning during the sign-in process. If you receive the warning, select Yes or Continue to proceed with the connection.
-
On the ContosoPrivate VM, map the Azure file share to drive Z using PowerShell ISE. Before running the commands that follow, REPLACE “storage-account-key”, and “storage-account-name” (i.e. contosostoragexx) with values you supplied and retrieved in the Create a storage account task.
Replace the “<Contents>” leaving the speech marks.
$acctKey = ConvertTo-SecureString -String "<storage-account-key>" -AsPlainText -Force
$credential = New-Object System.Management.Automation.PSCredential -ArgumentList "Azure\<storage-account-name>", $acctKey
New-PSDrive -Name Z -PSProvider FileSystem -Root "\\<storage-account-name>.file.core.windows.net\marketing" -Credential $credential -Persist
The Azure file share successfully mapped to the Z drive.
- Confirm that the VM has no outbound connectivity to the internet from a command prompt:
ping bing.com
You receive no replies because the network security group associated to the Private subnet does not allow outbound access to the internet.
- Close the remote desktop session to the ContosoPrivate VM.
Confirm access is denied to storage account
-
Enter ContosoPublic In the Search resources, services, and docs box at the top of the portal.
-
When ContosoPublic (Virtual machine) appears in the search results, select it.
-
Repeat steps 1-6 from Task 10: Confirm access to storage account task for the ContosoPublic VM.
After a short wait, you receive a New-PSDrive : Access is denied error. Access is denied because the ContosoPublic VM is deployed in the Public subnet. The Public subnet does not have a service endpoint enabled for Azure Storage. The storage account only allows network access from the Private subnet, not the Public subnet.
-
Confirm that the public VM does have outbound connectivity to the internet from a command prompt:
ping bing.com
-
Close the remote desktop session to the ContosoPublic VM.
-
From your computer, browse to the Azure portal.
-
Enter the name of the storage account you created in the Search resources, services, and docs box. When the name of your storage account appears in the search results, select it.
-
Select File shares then select the marketing file share.
-
You receive the error shown in the following screenshot:
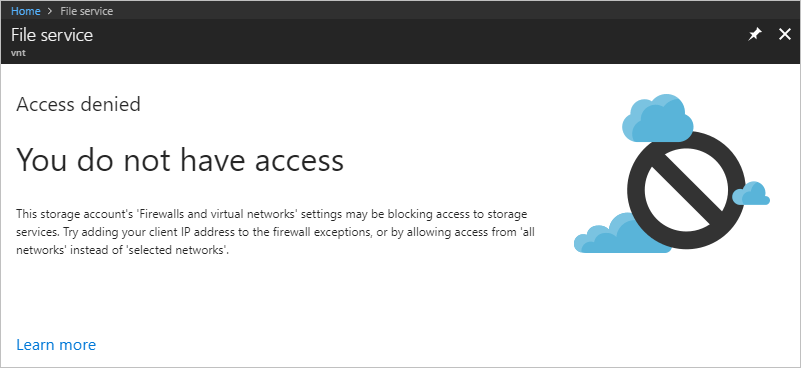
Access is denied, because your computer is not in the Private subnet of the CoreServicesVNet virtual network.
Warning: Prior to continuing you should remove all resources used for this lab. To do this On the Azure portal select Resource groups. Select any resources groups you have created. On the resource group blade select Delete Resource group, enter the Resource Group Name and select Delete. Repeat the process for any additional Resource Groups you may have created. Failure to do this may cause issues with other labs.
Results: You have now completed this lab.
Task 11: Clean up resources
Note: Remember to remove any newly created Azure resources that you no longer use. Removing unused resources ensures you will not see unexpected charges.
-
On the Azure portal, open the PowerShell session within the Cloud Shell pane.
-
Delete all resource groups you created throughout the labs of this module by running the following command:
Remove-AzResourceGroup -Name 'myResourceGroup' -Force -AsJobNote: The command executes asynchronously (as determined by the -AsJob parameter), so while you will be able to run another PowerShell command immediately afterwards within the same PowerShell session, it will take a few minutes before the resource groups are actually removed.